The cost of cybercrime is projected to hit an annual $10.5 trillion by 2025. It’s clear by this measure that organizations across all industries should be taking action to address their cybersecurity postures.
The fourth annual edition of Microsoft’s Digital Defense Report (MDDR), published in October 2023, highlights both the highs and lows of progress made to our collective digital defenses over the 2022-2023 year period. The report covers a vast array of discussion points, from gender inequality in the cybersecurity industry to the intricacies of Nation state attacks.
Above all, the report goes to great lengths to provide data-driven, actionable takeaways. Several guidelines detail steps that businesses and individuals can take to increase their defensive postures, including educational and implementation suggestions.
Here are some of the most applicable:
Collaboration is Key
The MDDR report states that “well‑resourced cybercriminal syndicates also continue to grow and evolve, leveraging the cybercrime-as-a-service ecosystem.” Both ransomware‑as‑ a-service and phishing-as-a-service are key threats to businesses, and both are growing in popularity.
There has been, however, increased global law enforcement resources.
Governments across the globe are providing the public with more information about cyber threats and how to counter them—for example, CISA’s Shields Up and Cybersecurity Awareness Month campaigns. Governments are also imposing new legal and regulatory requirements for cybersecurity, meaning that businesses must establish cybersecurity postures for legal compliance and to avoid fines.
The result is that globally, vendors are taking steps to improve the security of their digital products and services, and developing new tools to help their customers better defend against attackers. The combined efforts of governments, businesses, and individuals is leading to stronger overall security.
Human Weaknesses Are Still Common
In Chapter Two, “The State of Cybercrime,” the report details key changes to the existing cybercrime landscape. Cybercriminals have stayed focused on exploiting weaknesses in humans and how they use technology, and the top three threats identified by Microsoft Defender Experts this year were: identity attacks, ransomware encounters, and targeted phishing attacks.
Identity related attacks included traditional brute-force attempts, password spraying attacks, and adversary-in-the middle (AiTM) attacks. Ransomware encounters and targeted phishing attacks (often leading to malware) were both observed to be related to identity theft, which lines up with other patterns around stolen PII and credentials. The report shows that threat actors can leverage human psychology against us in manifold ways.
This emphasized the need for continued education, at multiple levels.
Identity Attacks Are Up, and Have Ramifications
According to Microsoft Entra data, the number of attempted password-based attacks “increased more than tenfold compared to the same period in 2022, from around 3 billion per month to over 30 billion.” The report said this translates to an average of four thousand password attacks per second targeting Microsoft cloud identities—expand this pattern to outside of Microsoft data and one can get an even more accurate idea about how prolific, and concerning, password based attacks are.
One of the main reasons password attacks are so prevalent is the low-security posture of many organizations. The MDDR reported that this is the case across all industries but particularly so in the education sector, saying “many of these organizations have not enabled MFA for their users, leaving them vulnerable to phishing, credential stuffing, and brute force attacks.” While MFA can act as a compensating control for compromised passwords, Enzoic’s research and other similar reports have shed light on an essential truth – the first and most crucial line of defense against password attacks is the strength and resilience of the passwords themselves.
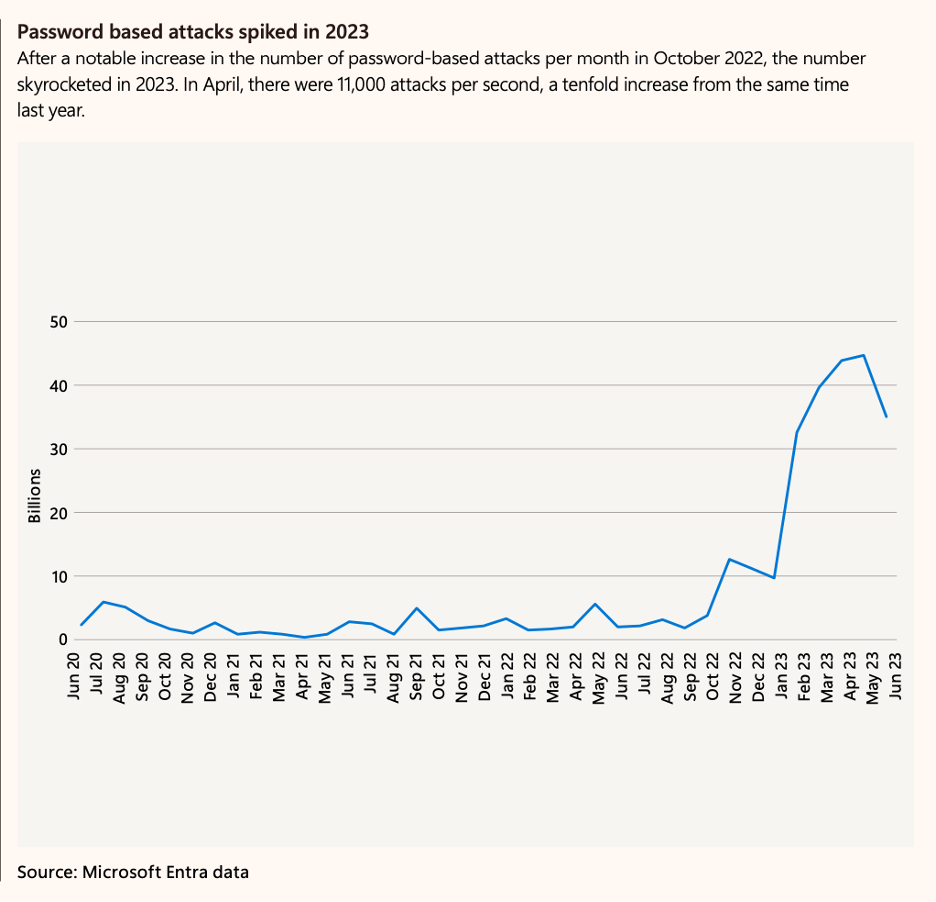
(MDDR 2023, pg 34)
The report recommended concrete action in relation to these attacks, echoing NIST guidelines: with Microsoft recommending the creation of strong passwords, using a password manager, and to change passwords immediately on accounts you suspect may have been compromised.
Increasing Resilience for Businesses of all Sizes
While the goal of all the suggested mitigations is to make systems more resilient to cyberattacks, the report makes a n astute observation: business owners may not always have the resources to implement all of the guidelines, nor the depth of knowledge to understand a return on their investment. They suggest that to aid with prioritization of cybersecurity tooling, generally speaking, “the lower the resources and effort involved, the higher the return on mitigation (ROM).” As an example of a high return, they offer the example of implementing MFA protection, saying
This solution is highly effective in preventing initial access (high security value) but very simple to implement (low effort). When implemented, this solution effectively prevents initial access by providing more context around the authentication attempt, such as geographic location and the application used.
Unfortunately, the report doesn’t have space to delve into the fact that MFA is only as strong as its weakest link. While it’s still certainly worth implementing, password security alone deserves a few paragraphs, given its ubiquitous nature.
The Digital Defense Report offers a glimpse into the depths of Microsoft’s threat research, and contains additional information about the applicability of AI-driven solutions, specifics on nation state attacks, and an encouraging promotion of additional open-source cyber tools for industry professionals. You can read the report here to find out more.