Enzoic’s proprietary research is powered by a combination of human and automated intelligence to rapidly provide clients with the most complete protection from credential based attacks.
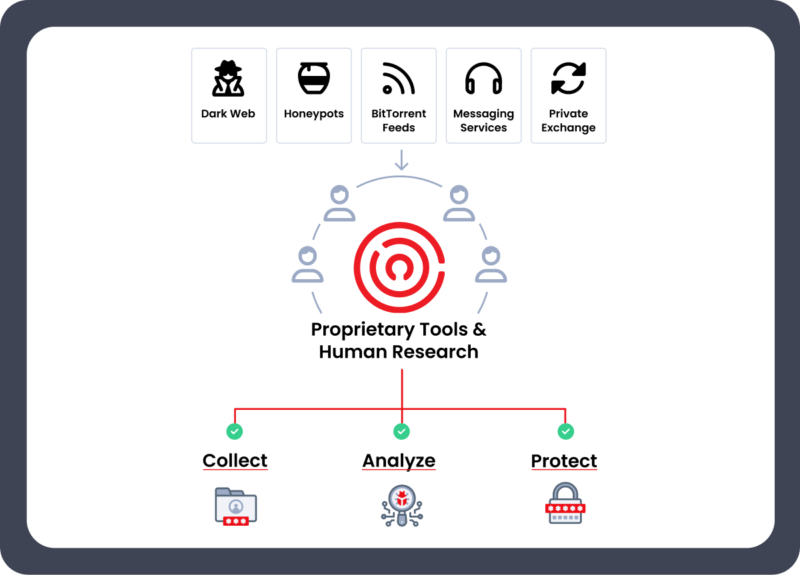
Enzoic uses multiple threat research techniques. Our trained analysts scour the public Internet, Dark Web and work with private sources. We’ve also developed proprietary tools that automatically scrape and download, including from short-lived sites. In addition, honeypots add credentials not available elsewhere by collecting in real-time from actual cyber-attacks underway. This combination of methods dramatically reduces the effective attack window.
While some services rely on clear text and crackable hashes, Enzoic offers a unique approach that allows comparisons to the original hash. This allows the use of uncrackable hashes, substantially increasing the breadth of Enzoic’s coverage. This provides additional security for our clients.
Our award-winning threat research is focused on fueling the use cases that protect against credential based attacks. This keeps our database clean from duplicated credential records, spam lists and data that would otherwise lead to unnecessary alert fatigue.
Our database contains breaches of all sizes. It goes beyond the well-publicized breaches to collect the numerous small data breaches that make no headlines but present outsized risks to individuals and organizations.
Enzoic’s proprietary technologies quickly normalize, deduplicate and index new exposures, providing our clients with the most current and complete protection. Our credentials and passwords database is updated multiple times each day.
231,743
80%
72%
4.1
26,000
Make detecting and eliminating compromised passwords in Active Directory easy with a simple plug-in. Start protecting for free.
Try Now